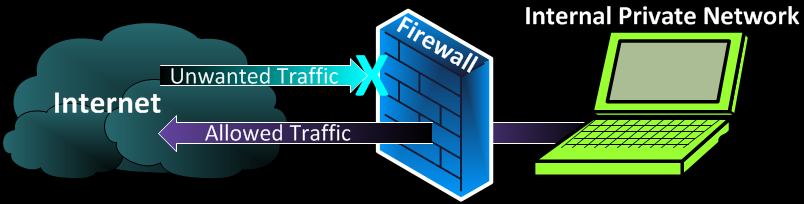
A firewall is a security system (which can be a hardware or software) that monitors and controls incoming and outgoing network traffic based on a set of security rules. It acts as a barrier between a trusted internal network (such as a corporate or home network) and untrusted external networks (like the internet) to prevent unauthorized access and potential threats.
Why are firewalls important?
Just as we hire security guards to monitor and prevent illegal activities like theft in our office or home, we need a firewall to secure our digital data. It monitors network traffic and allows or blocks it based on predefined security rules. Some points are given that’s make the firewall necessary.
- Firewalls prevent unauthorized access to a network, protecting sensitive data from external threats.
- They help manage and filter network traffic, ensuring only legitimate communications reach the network.
- Firewalls protect systems from various cyber-attacks such as Distributed Denial of Service (DDoS), malware etc.
How does a firewall work?
A firewall works by filtering and controlling the flow of network traffic between different networks, such as between a trusted internal network and an untrusted external network (like the internet). It inspects data packets and decides whether to allow or block them based on predefined security rules. Here’s a more detailed breakdown of how it works:Packet Filtering
The firewall examines each incoming and outgoing data packet, looking at the packet’s header to assess its source IP address, destination IP address, protocol type, and port number. If the packet matches an allowed rule, it is permitted to pass through. If it matches a block rule, it is discarded.
Stateful Packet Inspection
Stateful packet inspection goes beyond simple packet filtering by tracking TCP or UDP sessions between devices. For example, it can monitor connections originating from the trusted network. This session information is stored in a state table, allowing temporary openings in the firewall for return traffic, which would otherwise be blocked.
Proxy Services
Firewall can also act as a proxy by making requests on behalf of another device. It essentially serves as a middleman for communication between devices.
Network Address Translation
Network Address Translation (NAT) hides the internal IP addresses of a network by using a single external IP address, adding an extra layer of security by making it more difficult for attackers to target internal systems.
Access Control
Firewalls enforce rules that specify who can access the network and what services they can use. These rules can be based on factors like IP addresses, ports, applications, and users. For example, a firewall may allow web traffic (HTTP/HTTPS) but block FTP or SSH connections to the internal network.
Raghav Rajput
With a strong academic background, including an MCA and CEH certification, I bring over two years of hands-on experience in cybersecurity. In my role, I focus on Android, iOS, and web penetration testing, consistently applying advanced skills to safeguard digital landscapes. Outside of work, I enjoy the intellectual challenge of chess and find relaxation in listening to music, which balances my passion for cybersecurity with personal growth and creativity.
Last Update: November 9, 2024





