Understanding Exported Activities and Intent Filters
In this blog, we dive into the world of Android app security by exploring exported activities and intent filters. These components, defined in the AndroidManifest.xml file, allow apps to interact with each other but can also expose your app to serious security risks if not properly configured. Learn how to identify exported activities, analyze intent filters, and understand the potential vulnerabilities they introduce.
Performing Static Testing on Android Applications
Learn how to perform static testing on Android applications to identify vulnerabilities, hardcoded secrets, and insecure configurations. Explore tools, steps, and best practices for secure app development.
Setting Up Your Android Penetration Testing Lab
Setting up a dedicated lab is your first step towards uncovering the vulnerabilities of Android applications in a safe and ethical manner.
Latest Articles
Understanding Exported Activities and Intent Filters
In this blog, we dive into the world of Android app security by exploring exported activities and intent filters. These components, defined in the AndroidManifest.xml file, allow apps to interact with each other but can also expose your app to serious security risks if not properly configured. Learn how to identify exported activities, analyze intent filters, and understand the potential vulnerabilities they introduce.
Performing Static Testing on Android Applications
Learn how to perform static testing on Android applications to identify vulnerabilities, hardcoded secrets, and insecure configurations. Explore tools, steps, and best practices for secure app development.
Setting Up Your Android Penetration Testing Lab
Setting up a dedicated lab is your first step towards uncovering the vulnerabilities of Android applications in a safe and ethical manner.
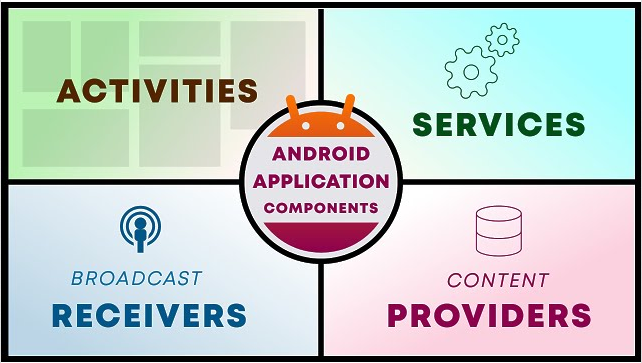
Overview of Android app components (Activities, Services, Broadcast Receivers, Content Providers)
Android applications are built using four main components, each with a unique role in the app’s functionality. Understanding these components…
Introduction to Android PT: Exploring the Kernel and OS Architecture
Dive into the world of Android penetration testing, where the intricacies of the kernel and OS architecture come to life! Discover how the layered architecture—from the Linux kernel to the applications layer
What is a Firewall and How Does It Work?
A firewall is a security system (which can be a hardware or software) that monitors and controls incoming and outgoing…
Decoding Cybersecurity: A Beginner’s Guide to Key Terms – Part 2
Vulnerability Assessment is to identify, quantify, and prioritize vulnerabilities in a system, application, or network. It focuses on finding potential weaknesses without exploiting them.
Decoding Cybersecurity: A Beginner’s Guide to Key Terms
Authentication is the process of verifying your identity using methods such as passwords, biometrics, or security keys. For example, logging in with a username and password or unlocking your phone with a thumbprint are forms of authentication.
What is Cyber Security?
Cybersecurity is the practice of protecting computer systems, networks, and data from cyber threats such as hacking, data breaches, and unauthorized access. It involves the implementation of security measures like firewalls, encryption, and secure access controls to protect sensitive information.