In the last blog, we decompiled the APK and assigned you the task of analyzing the code to identify vulnerabilities on your own. In this blog, we will focus on analyzing the manifest file and identifying all the vulnerabilities it contains. The code of manifest.xml is given below.
<?xml version="1.0" encoding="utf-8"?>
<manifest xmlns:android="http://schemas.android.com/apk/res/android"
android:versionCode="1"
android:versionName="1.0"
package="jakhar.aseem.diva"
platformBuildVersionCode="23"
platformBuildVersionName="6.0-2166767">
<uses-sdk
android:minSdkVersion="15"
android:targetSdkVersion="23"/>
<uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.READ_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.INTERNET"/>
<application
android:theme="@style/AppTheme"
android:label="@string/app_name"
android:icon="@mipmap/ic_launcher"
android:debuggable="true"
android:allowBackup="true"
android:supportsRtl="true">
<activity
android:theme="@style/AppTheme.NoActionBar"
android:label="@string/app_name"
android:name="jakhar.aseem.diva.MainActivity">
<intent-filter>
<action android:name="android.intent.action.MAIN"/>
<category android:name="android.intent.category.LAUNCHER"/>
</intent-filter>
</activity>
<activity
android:label="@string/d1"
android:name="jakhar.aseem.diva.LogActivity"/>
<activity
android:label="@string/d2"
android:name="jakhar.aseem.diva.HardcodeActivity"/>
<activity
android:label="@string/d3"
android:name="jakhar.aseem.diva.InsecureDataStorage1Activity"/>
<activity
android:label="@string/d4"
android:name="jakhar.aseem.diva.InsecureDataStorage2Activity"/>
<activity
android:label="@string/d5"
android:name="jakhar.aseem.diva.InsecureDataStorage3Activity"/>
<activity
android:label="@string/d6"
android:name="jakhar.aseem.diva.InsecureDataStorage4Activity"/>
<activity
android:label="@string/d7"
android:name="jakhar.aseem.diva.SQLInjectionActivity"/>
<activity
android:label="@string/d8"
android:name="jakhar.aseem.diva.InputValidation2URISchemeActivity"/>
<activity
android:label="@string/d9"
android:name="jakhar.aseem.diva.AccessControl1Activity"/>
<activity
android:label="@string/apic_label"
android:name="jakhar.aseem.diva.APICredsActivity">
<intent-filter>
<action android:name="jakhar.aseem.diva.action.VIEW_CREDS"/>
<category android:name="android.intent.category.DEFAULT"/>
</intent-filter>
</activity>
<activity
android:label="@string/d10"
android:name="jakhar.aseem.diva.AccessControl2Activity"/>
<activity
android:label="@string/apic2_label"
android:name="jakhar.aseem.diva.APICreds2Activity">
<intent-filter>
<action android:name="jakhar.aseem.diva.action.VIEW_CREDS2"/>
<category android:name="android.intent.category.DEFAULT"/>
</intent-filter>
</activity>
<provider
android:name="jakhar.aseem.diva.NotesProvider"
android:enabled="true"
android:exported="true"
android:authorities="jakhar.aseem.diva.provider.notesprovider"/>
<activity
android:label="@string/d11"
android:name="jakhar.aseem.diva.AccessControl3Activity"/>
<activity
android:label="@string/d12"
android:name="jakhar.aseem.diva.Hardcode2Activity"/>
<activity
android:label="@string/pnotes"
android:name="jakhar.aseem.diva.AccessControl3NotesActivity"/>
<activity
android:label="@string/d13"
android:name="jakhar.aseem.diva.InputValidation3Activity"/>
</application>
</manifest>
Root Element
From line 2-7, manifest file contain basic information like versionName, versionCode, Unique Identifier(Package Name) and version of the Android SDK used to build the app.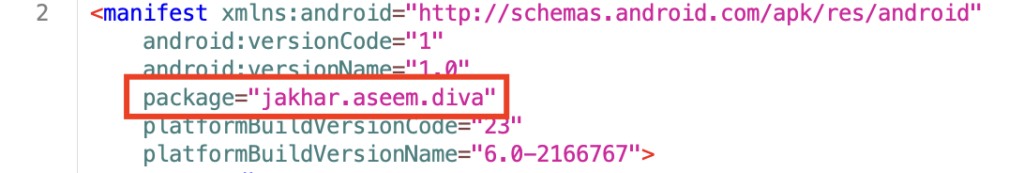
<uses-sdk>
From line 8-10, Specifies the minimum Android version required to run the app and the API level the app is optimized for. This application can be installed on older versions of Android (4.0.3 and above), which have multiple unresolved vulnerabilities. Devices running these versions no longer receive regular security updates from Google. As a result, if the application is installed on such devices, it becomes susceptible to exploitation.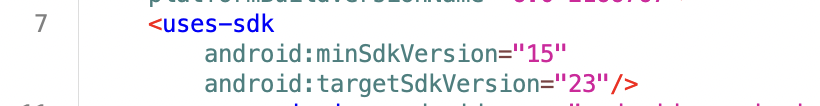
<uses-permission>
Declares the permissions the app requires.- WRITE_EXTERNAL_STORAGE: Allows writing to external storage (e.g., SD card). Can be exploited if sensitive data is stored insecurely.
- READ_EXTERNAL_STORAGE: Allows reading from external storage.
- INTERNET: Allows the app to access the internet.

<application>
- android:theme: Specifies the app’s theme.
- android:label: defines app name
- android:icon: The app’s launcher icon, defined in a drawable resource (
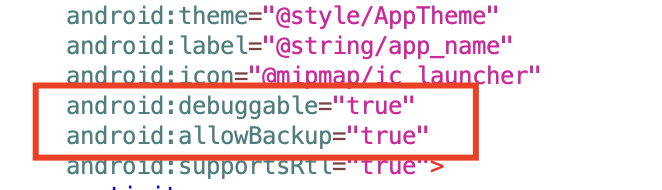
@mipmap/ic_launcher). - android:debuggable=”true”: Indicates the app is in debug mode. This is a security risk in production, as it allows attackers to debug the app.
- android:allowBackup=”true”: Allows the app’s data to be backed up. This can be exploited to retrieve sensitive data.
- android:supportsRtl=”true”: Indicates the app supports right-to-left (RTL) layouts for languages like Arabic.
Raghav Rajput
With a strong academic background, including an MCA and CEH certification, I bring over two years of hands-on experience in cybersecurity. In my role, I focus on Android, iOS, and web penetration testing, consistently applying advanced skills to safeguard digital landscapes. Outside of work, I enjoy the intellectual challenge of chess and find relaxation in listening to music, which balances my passion for cybersecurity with personal growth and creativity.
Last Update: December 30, 2024