Setting up a dedicated lab is your first step towards uncovering the vulnerabilities of Android applications in a safe and ethical manner.
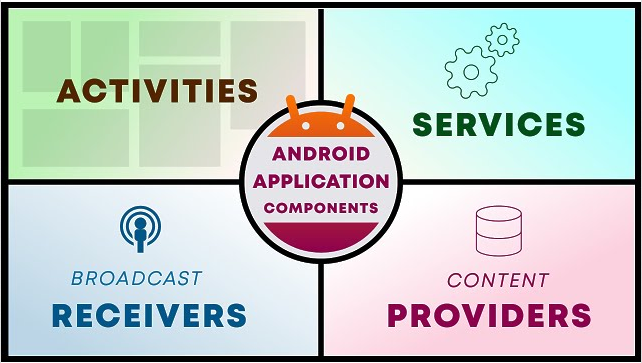
Android applications are built using four main components, each with a unique role in the app’s functionality….
Dive into the world of Android penetration testing, where the intricacies of the kernel and OS architecture come to life! Discover how the layered architecture—from the Linux kernel to the applications layer
A firewall is a security system (which can be a hardware or software) that monitors and controls…
Vulnerability Assessment is to identify, quantify, and prioritize vulnerabilities in a system, application, or network. It focuses on finding potential weaknesses without exploiting them.